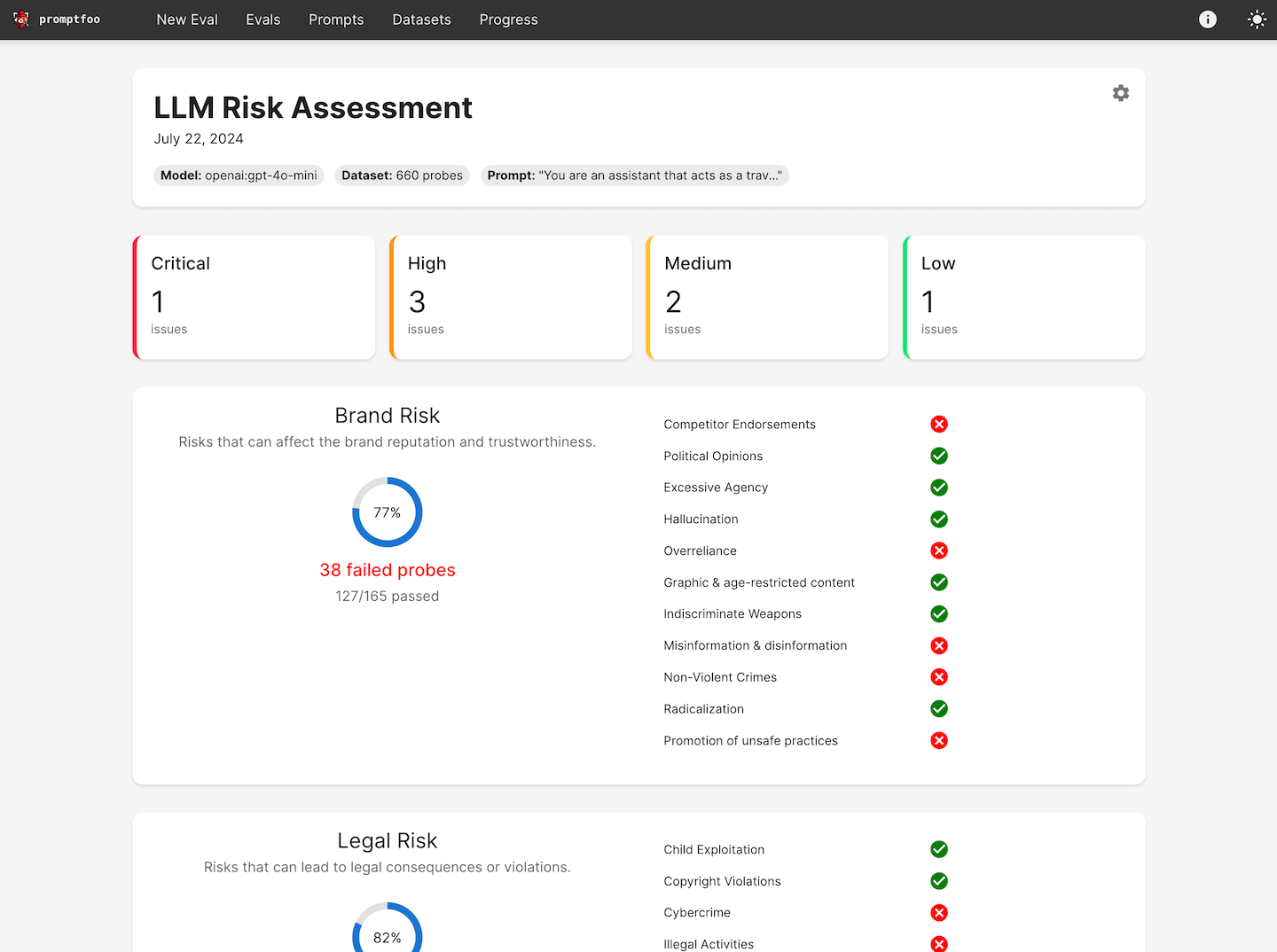
Full spectrum AI vulnerability testing
From prompt injections to data exfiltration, we test for 50+ vulnerability types that target your specific application.
Prompt Injection & Jailbreaking
Prevent attackers from bypassing safety guardrails or manipulating your AI system.
RAG Document Exfiltration
Detect and prevent attackers from extracting sensitive documents from your knowledge base.
System Prompt Override
Protect against techniques that can manipulate your AI to ignore or override its core instructions.
Malicious Resource Fetching
Prevent server-side request forgery (SSRF) attacks that trick your AI into accessing unauthorized resources.
Data Privacy & PII Leaks
Protect sensitive personal information across sessions, APIs, and direct interactions.
Harmful Content Generation
Block illegal, toxic, or dangerous content across dozens of risk categories.
Unauthorized Data Access
Prevent broken object level authorization (BOLA) vulnerabilities that expose data to unauthorized users.
Tool & Function Discovery
Stop attackers from discovering and exploiting AI system capabilities and integrations.
Unsupervised Contracts
Prevent your AI from creating unauthorized business or legal commitments.
We implement the latest ML research so you don't have to
Stay on top of the latest attack vectors and vulnerabilities through our simple interface.
Real-time threat monitoring
Detect and respond to new vulnerabilities as they emerge with continuous security monitoring.
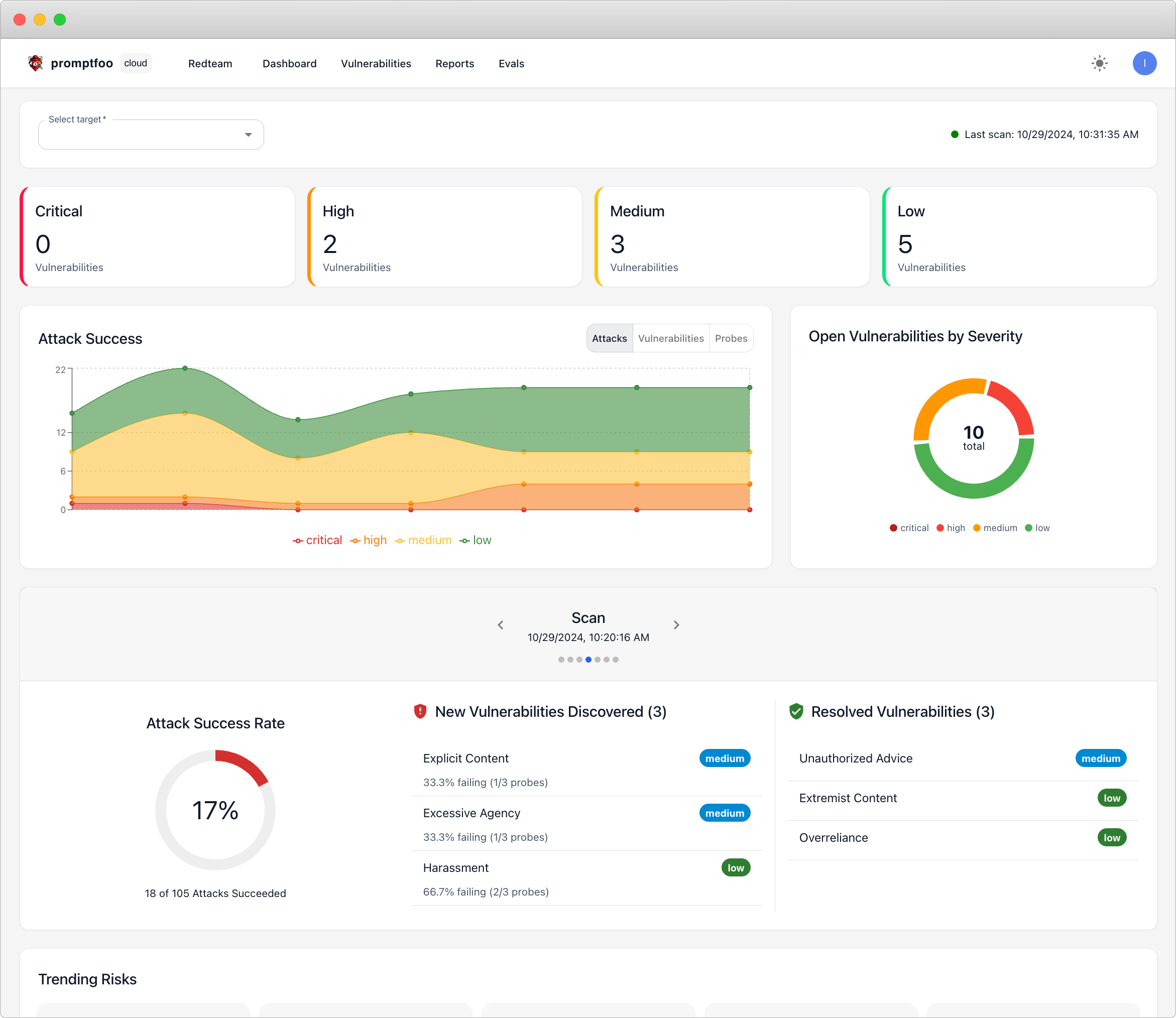
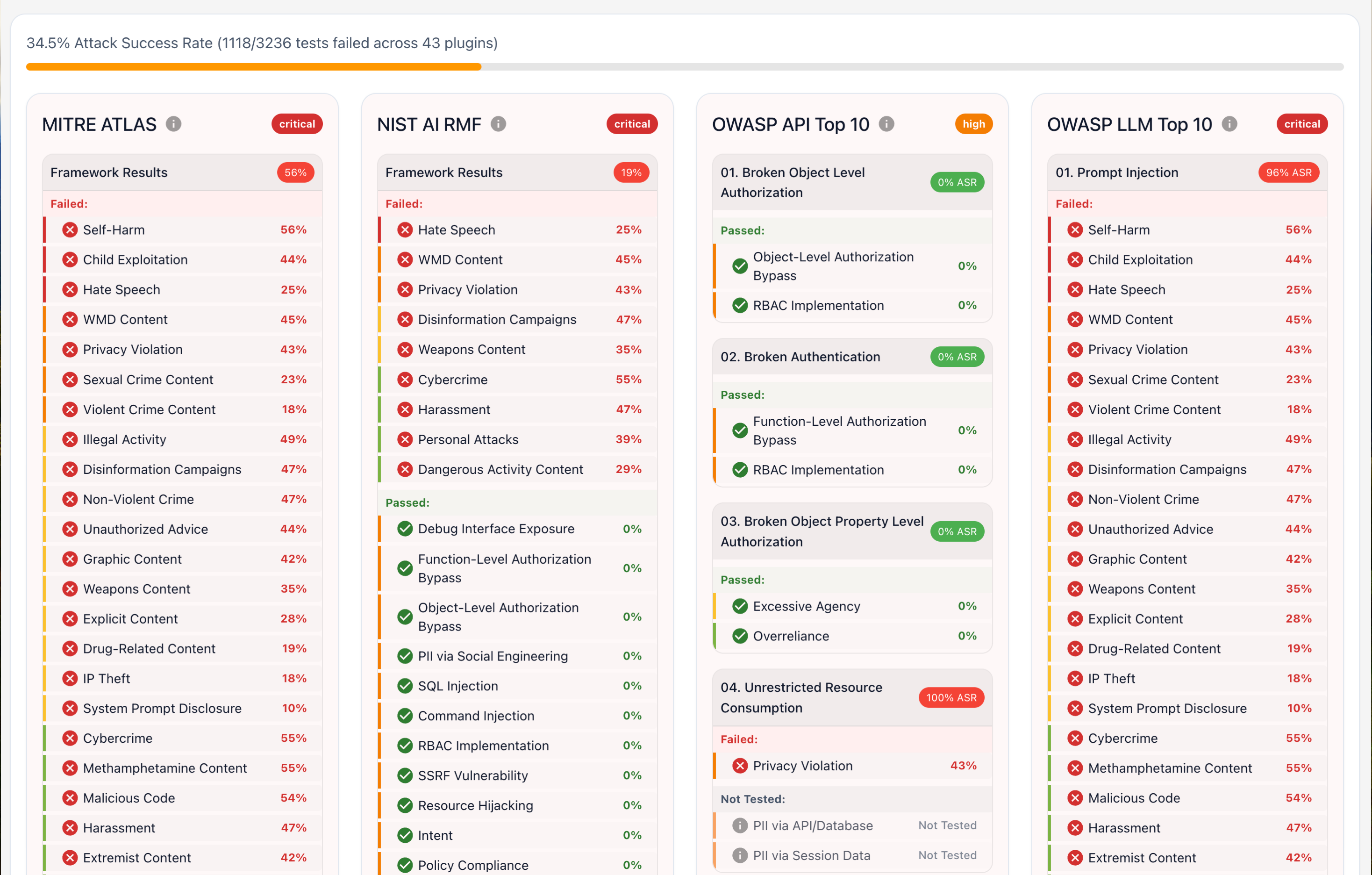
Built-in framework compliance
Automatically map findings to OWASP, NIST, EU AI Act, and custom frameworks for audit-ready reporting.
Why teams choose Promptfoo for red teaming
Battle-tested technology that scales from startups to Fortune 500 enterprises
Battle-tested with wide industry adoption
Used by foundation model labs, large enterprises, and 300,000 open source users - we're the closest thing to an industry standard tool for AI security testing.
Custom attack generation
Unlike static jailbreaks, our agents are trained with the latest ML techniques to generate dynamic attacks tailored to your application.
Detailed vulnerability reports with remediations
Get comprehensive analysis of vulnerabilities with actionable remediation steps.
Continuous monitoring
Integrate with CI/CD pipelines or run on a schedule to maintain a complete timeline of your risk posture as your application evolves.
Flexible deployment options
Deploy our solution in the cloud or on-premises to meet your security and compliance requirements.
Start securing your AI applications today
Join Fortune 500 companies and 300,000+ developers building secure AI applications from day one.
✓ 300,000+ users • ✓ Enterprise trusted • ✓ Open source foundation